IBM’s Threat Hunting, designing for lurking threats.
At IBM, the goal was to streamline and empower threat hunting for security analysts working across complex environments. Using IBM Cloud Pak for Security, we unified threat data from disparate tools and sources into a centralized, intuitive interface—eliminating silos and reducing investigation time.
We collaborated closely with Tier 1 and Tier 2 SOC analysts to understand the pain points in their workflows. Through user research, journey mapping, and iterative prototyping, we identified key needs: rapid signal triage, intuitive threat correlation, and the ability to pivot quickly across data sets without switching tools.
Our solution focused on:
Federated search across multiple data sources without moving the data
Integrated threat intelligence and MITRE ATT&CK mapping
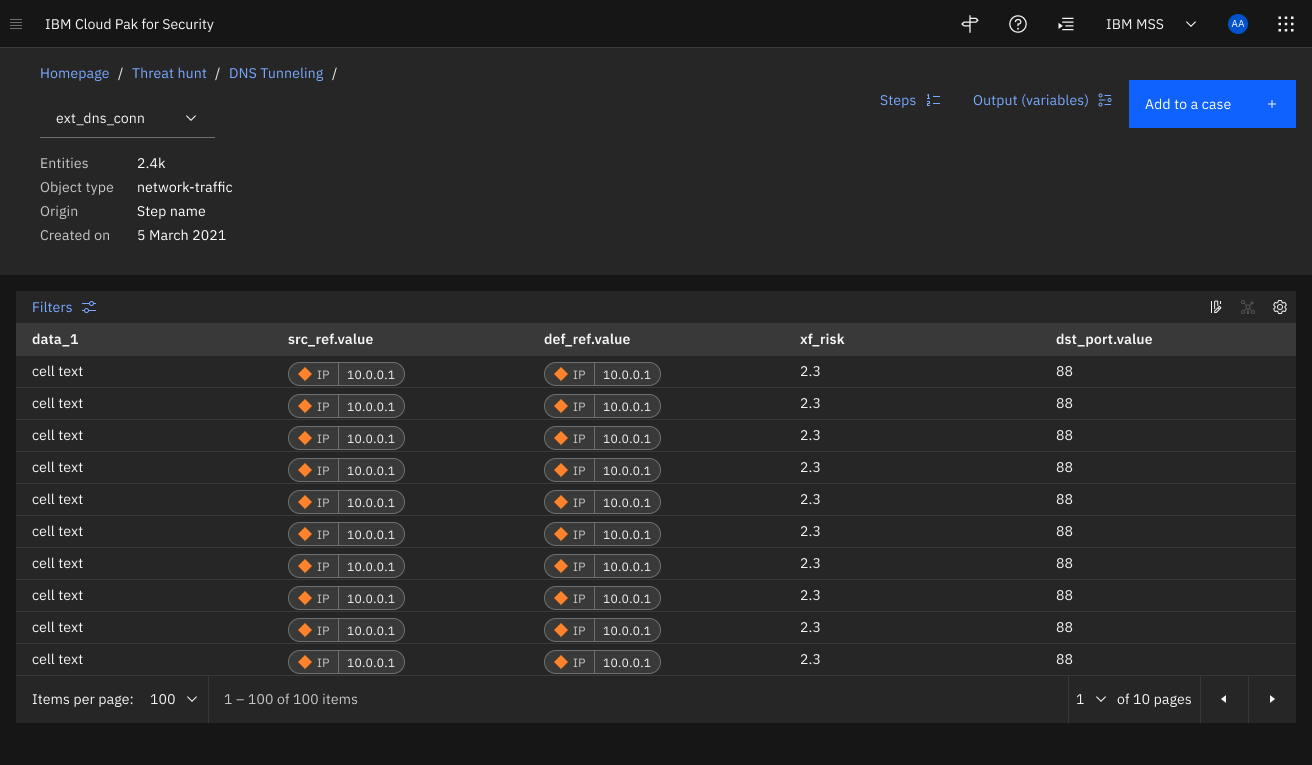
Visual link analysis to identify relationships between entities
Automated investigation playbooks to reduce manual effort
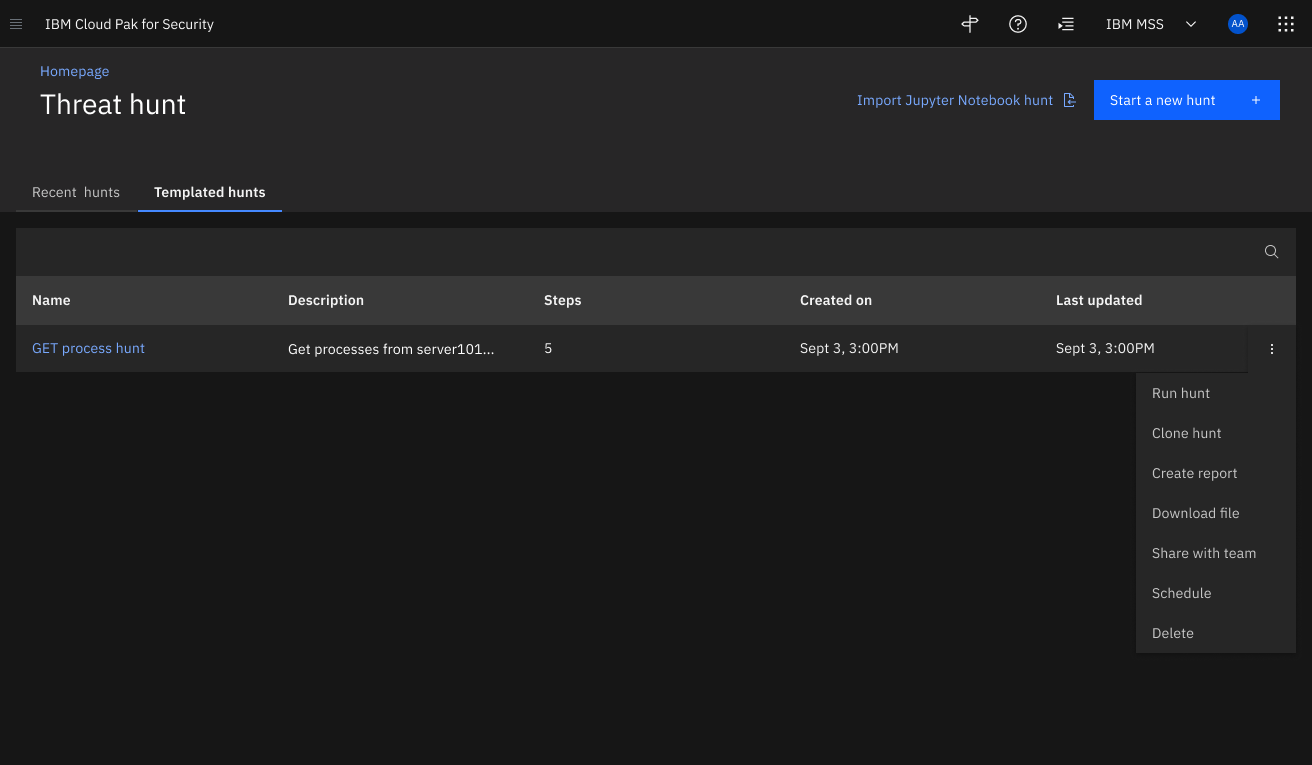
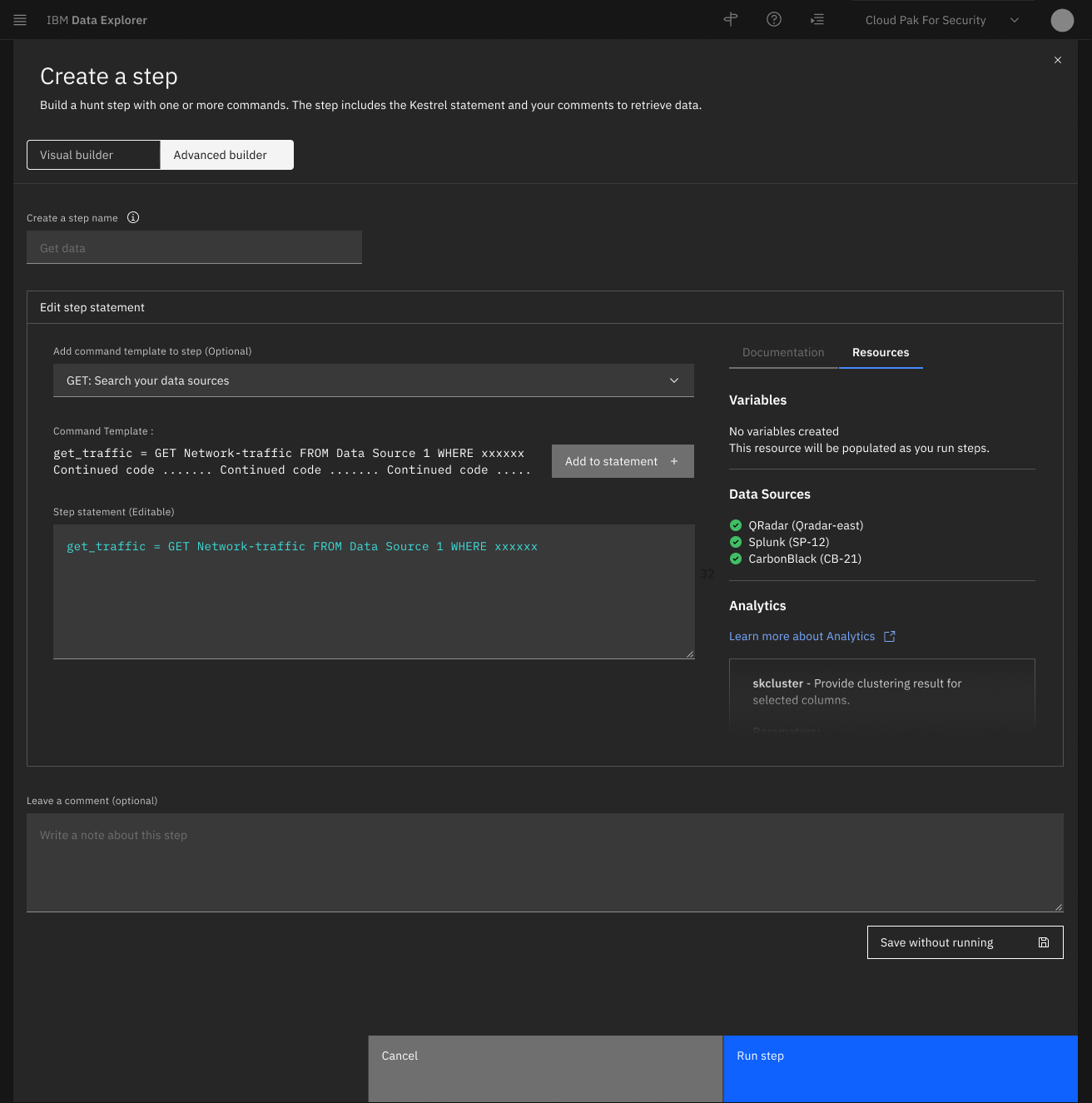
Simple and advanced step builders for all SOC analysts
The result was a more efficient and confident threat hunting experience, enabling analysts to detect, investigate, and respond to advanced threats faster and with greater context.
As the Design Lead for this project, I drove the overall design strategy, mentored new designers in both product and domain expertise, and collaborated cross-functionally with user researchers, designers, product managers, product owners, data analysts, developers, and SMEs. I also led retrospectives and sprints, ensuring full team engagement throughout the process, from ideation to implementation.
If you’re curious about our process or want to learn more about the solutions we explored, feel free to reach out. Here are some screens for a view of the system.
Company
IBM
Threat Hunt - IBM Cloud Pak for Security
Roles
Lead Senior Designer, I led a team of designers and researchers.
Concept / UX / Prototyping / Storytelling / Cyber-Security domain
Year
2023-2024
Entry point
Templates of hunts
Create a step for hunt
Output (variable) view with column customization